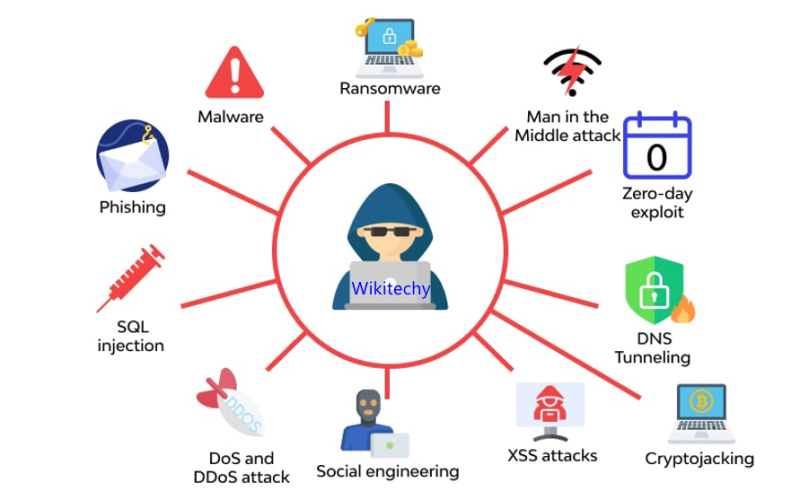
Introduction:
As a cybersecurity analyst with a passion for defending digital landscapes, I’ve seen firsthand how cybersecurity is evolving to address new and sophisticated threats. This article delves into how cybersecurity is adapting to these emerging threats, highlighting innovative defenses and strategies essential for protecting sensitive information in an increasingly digital world.
The Rise of AI-Driven Attacks
Explore the emergence of AI-driven attacks. Discuss how cybercriminals are leveraging artificial intelligence to launch more sophisticated and adaptive attacks, including deepfake scams, AI-powered phishing, and automated exploitation of vulnerabilities.
Advanced Persistent Threats (APTs)

Examine the growing threat of advanced persistent threats. Explain how APTs involve prolonged and targeted cyberattacks, often backed by nation-states or organized cybercriminal groups, aimed at stealing sensitive information or sabotaging critical infrastructure.
Zero-Day Exploits
Discuss the significance of zero-day exploits in modern cybersecurity. Highlight how attackers exploit unknown vulnerabilities in software before developers can issue patches, emphasizing the need for proactive vulnerability management and timely updates.
Strengthening Endpoint Security
Analyze the importance of endpoint security in defending against new threats. Discuss how organizations are implementing advanced endpoint protection solutions, including next-generation antivirus, endpoint detection and response (EDR), and behavior analytics to detect and mitigate threats at the device level.
Embracing Zero Trust Architecture
Explore the adoption of zero trust architecture as a defense strategy. Explain the zero trust model, which assumes no user or device is inherently trusted, and discuss how organizations are implementing strict access controls, continuous monitoring, and micro-segmentation to enhance security.
Enhancing Threat Intelligence
Examine the role of threat intelligence in adapting to new threats. Discuss how organizations are leveraging threat intelligence platforms to collect, analyze, and share information about emerging threats, enabling proactive defenses and informed decision-making.
The Role of Machine Learning in Cybersecurity

Analyze the impact of machine learning on cybersecurity. Discuss how machine learning algorithms are used to detect anomalies, identify patterns in large datasets, and predict potential threats, enhancing the ability to respond to sophisticated attacks quickly.
Strengthening Cloud Security
Discuss the importance of cloud security in the modern threat landscape. Highlight how organizations are securing their cloud environments by implementing robust access controls, encryption, continuous monitoring, and compliance with industry standards.
Addressing the Human Factor
Examine the human factor in cybersecurity. Discuss the importance of cybersecurity awareness training, employee education, and fostering a culture of security within organizations to mitigate the risk of human error and social engineering attacks.
Future Trends in Cybersecurity
Conclude with a forward-looking perspective on future trends in cybersecurity. Discuss emerging technologies and strategies, such as quantum cryptography, blockchain security, and autonomous threat response, that promise to shape the future of cybersecurity.
Informative Table: Key Strategies in Modern Cybersecurity
| Strategy | Description | Examples |
| AI-Driven Defenses | Using AI to detect and respond to threats | Machine learning algorithms, anomaly detection |
| Zero Trust Architecture | Assumes no user or device is trusted by default | Strict access controls, continuous monitoring |
| Endpoint Protection | Securing devices from threats | Next-gen antivirus, EDR solutions |
| Threat Intelligence | Gathering and analyzing data on emerging threats | Threat intelligence platforms, information sharing |
| Cloud Security | Protecting cloud environments | Encryption, access controls, compliance checks |
Comparative Table: Traditional vs. Modern Cybersecurity Approaches
| Aspect | Traditional Approach | Modern Approach |
| Threat Detection | Signature-based antivirus | AI and machine learning-based detection |
| Network Security | Perimeter defenses (firewalls) | Zero trust architecture, micro-segmentation |
| Incident Response | Manual analysis and response | Automated threat response, SOAR platforms |
| User Authentication | Passwords | Multi-factor authentication, biometric verification |
| Data Protection | Data encryption at rest | End-to-end encryption, data tokenization |
Conclusion: Navigating the Future of Cybersecurity
The cybersecurity landscape is continually evolving to address new and sophisticated threats. By leveraging advanced technologies such as AI, machine learning, and zero trust architecture, and by enhancing endpoint security, threat intelligence, and cloud security, organizations can better defend against emerging cyber threats.
Additionally, addressing the human factor and fostering a culture of security are crucial in creating a resilient cybersecurity posture. As we look to the future, embracing innovative strategies and staying ahead of cybercriminals will be essential in safeguarding our digital world.